Threat actors have a new tactic — and it could raise the risk of phishing attacks at your company.
The tactic? ZeroFont phishing. It enables malicious emails to slip past Microsoft Outlook’s email-scanning system while simultaneously fooling recipients that the message is secure.
How can you prevent your employees from falling prey to ZeroFont phishing?
What Are ZeroFont Phishing Attacks?
ZeroFont phishing isn’t exactly new, but the way threat actors are using it now is.
First, let’s examine what ZeroFont phishing is and how it was originally used.
What is ZeroFont Phishing?
What’s the best way to evade Microsoft’s Office 365 Advanced Threat Protection (ATP)?
Shrink your email font to zero.
Hence the name, “ZeroFont phishing.” These tiny fonts are imperceptible to the human eye but not to AI and natural language processing (NLP) algorithms. Part of Microsoft’s ATP, these algorithms are responsible for scanning and filtering emails to protect Outlook users from malware attachments and links to malicious websites. They scan and analyze zero-sized fonts.
Zero-sized fonts enable cybercriminals to sprinkle benign words in between suspicious ones, throwing the NLP algorithms off their trail of deception.
ZeroFont Phishing Now
Why stop at fooling NLP algorithms, though? Especially when ZeroFont phishing works so well at evading cyber defense tools and giving recipients the illusion that their emails are safe.
In an evolution of the tactic, threat actors have begun simply writing something like, “Scanned and secured by ISCⓇ Advanced Threat Protection (ATP)” in zero-point font at the top of the email. The NLP algorithms in the email browser then populate Outlook’s preview pane with the message, giving users the impression that the email passed its security checks.
Of course, when recipients open the email, they don’t see the fake security scan text.
It’s too small to read. Instead, they’re met with a much more enticing message: a job offer or some other message that would encourage additional reading and click-through.
ZeroFont Phishing: Real-World Example
Below is a real-world example of ZeroFont phishing.
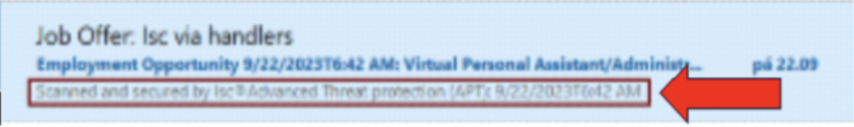
Let’s Start with the Email Preview Pane
What job seeker wouldn’t open this email? It holds the promise of employment, and it’s secure — or so it seems.
The preview pane message is really zero-font text at the top of the email.
Now Let’s Explore the Email Content
Open the email and there’s no sign of the securely scanned message in the preview pane. All recipients see is “Virtual Personal Assistant/Administrative Assistant.” Pretty sneaky, right?
ZeroFont Phishing: Another Demonstration Example
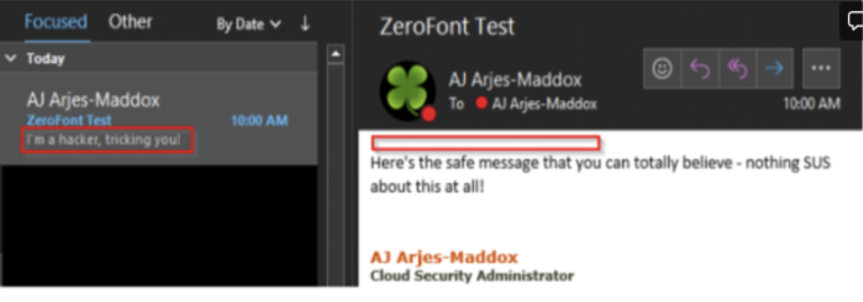
Here’s another example of ZeroFont phishing that GCS’ Cloud Security Administrator AJ Arjes-Maddox put together to demonstrate how the tactic works.
At the top of the email, he wrote, “I’m a hacker, tricking you!” in size zero font. It appears in Outlook’s preview pane but not in the email content.
How to Spot ZeroFont Phishing Attacks
The biggest lesson from the recent spate of ZeroFont phishing attacks? Don’t believe everything you read. Just because an email’s preview pane says it’s been “securely scanned” doesn’t mean it has.
Advise your employees to disregard such security messages and to scrutinize the email for these common phishing red flags:
Sender and Domain Name
Who sent the email? Do you recognize them? Is the domain correct — or slightly off? Typing your boss’ name in the “from line” is easy. Sending the email from your company domain isn’t.
Always check the sender’s domain name first.
Tone and Writing Style
If coworkers typically use an informal writing style and you get an email from one that’s overly formal — investigate further before clicking any links or sharing information. Message them on Teams or give them a call to verify they sent the email.
Grammar and Spelling
Grammar and spelling mistakes are telltale signs of phishing. However, that’s starting to change thanks to chatbots. Now, bad actors across the globe have the ability to generate nearly error-free content in English.
Still, watch out for misspelled words, odd phrasing, and misplaced commas. Spotting them could save you the time and headache of a phishing attack.
Urgency and Scarcity
Phishing emails often target recipients’ fears and desires: for example, fraud alerts. Or, as we saw with the ZeroFont phishing example, a job offer. Bad actors capitalize on the heightened emotions their emails trigger with urgency and scarcity. Think “click this link now to stop fraud” or “reply to this job offer in the next 24 hours.”
Be wary of such messages. Slow down. Examine the sender, domain, and content. Verify the information first. Whether that means calling your bank or investigating the organization sending the job offer.
Stay Safe, Especially During the Holiday Season
When retail prices drop, phishing scams spike. Stay vigilant for ZeroFont and other types of phishing attacks this holiday season. Advise your employees on these cybersecurity best practices too.
As always, GCS Technologies is here to provide the tools and training you need to keep your team safe.



