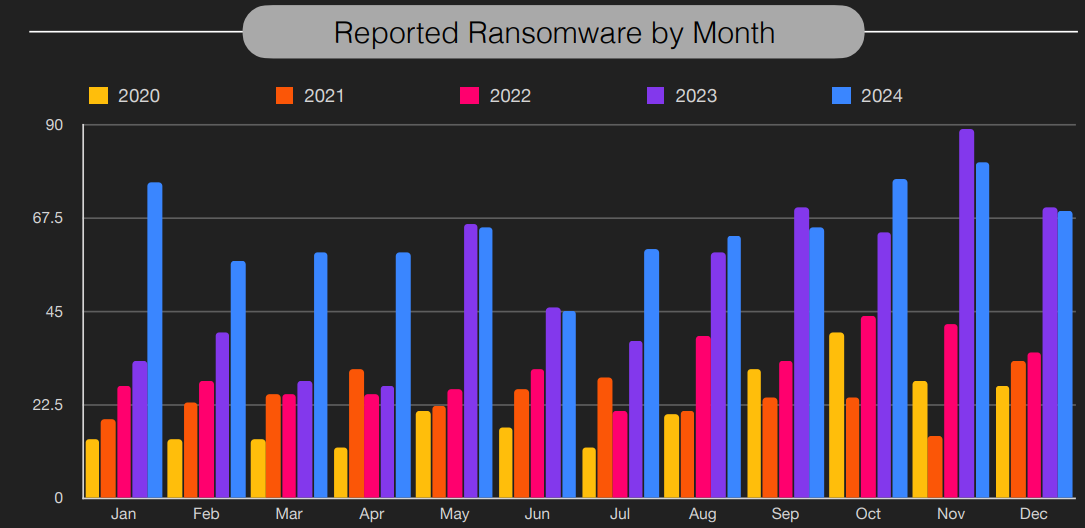
Over the past five years, ransomware trends have evolved into a persistent, high-cost threat that’s impossible to ignore. Ransomware activity in 2024 has consistently outpaced previous years, with October and November marking the highest spikes over the past five years. Failing to adapt your security strategy isn’t just a risk—it’s an invitation for disaster.
Image source: BlackFog Ransomware Report – December 2024
What this means for your business
No one is too small to be a target. Cybercriminals aren’t just going after large corporations anymore. A small law firm, a midsize manufacturer, or even a startup running on a lean IT budget—every organization is at risk. The focus isn’t on company size but system weaknesses. If your defenses are outdated, attackers will find a way in.
3 key ransomware trends to watch:
1. More sophisticated attack methods
Phishing emails may still be the most common delivery method, but today’s ransomware attacks are far more advanced. Cybercriminals use a combination of social engineering, exploiting unpatched software vulnerabilities, and even automation to launch targeted, multi-layered assaults. For example, attackers may impersonate a trusted vendor or colleague to gain initial access, then deploy ransomware that spreads across networks in minutes.
One alarming ransomware trend is the rise of “double extortion.” Here, attackers steal sensitive data before encrypting it and demand two ransoms: one for unlocking your systems and another to prevent the release of stolen data. The result? A threat that hits businesses on multiple fronts—financial loss, operational downtime, and reputational damage. These methods highlight the need for businesses to adopt proactive, adaptive defenses rather than relying on reactive measures.
2. Outdated security systems don’t stand a chance
Legacy antivirus software and perimeter defenses—once the cornerstone of business security—are no longer effective against modern ransomware trends. Ransomware doesn’t respect the traditional boundaries of firewalls or rely on simple malware files that can be easily quarantined. Today, attackers target endpoints, compromise user accounts, and infiltrate supply chains to bypass these outdated defenses.
For example, many companies that still rely on legacy systems have fallen victim to ransomware distributed through compromised remote access tools or outdated VPN configurations. Once inside, attackers exploit the lack of modern detection tools, encrypt data, and spread laterally across the network. Businesses must now implement layered defenses, such as Endpoint Detection and Response (EDR) tools and advanced threat intelligence, to stay ahead of evolving threats.
3. Human error remains the top entry point
Despite advancements in technology, employees continue to be a critical weak point in cybersecurity. Phishing emails remain the primary delivery method for ransomware, accounting for over 90% of attacks. Why? Because attackers exploit human curiosity and urgency, crafting emails that appear legitimate and demand immediate action, such as fake invoices, delivery notifications, or even messages impersonating the CEO.

For example, in a recent attack, a small manufacturing company lost access to its operations after an employee clicked on a link in a phishing email that appeared to come from their IT department. Within hours, ransomware encrypted their entire system, forcing them to pay tens of thousands of dollars to restore operations.
5 Practical steps to improve your security strategy
Statistics show ransomware isn’t slowing down and businesses that fail to adapt will remain vulnerable. The good news? You don’t need an unlimited budget to strengthen your defenses—just a strategic, layered approach. Here’s what you can do right now to reduce your risk:
1. Invest in Endpoint Protection
Traditional antivirus software can’t keep up with modern ransomware tactics. Attackers use fileless malware (software the operates entirely within the computer’s memory) and exploit system vulnerabilities to bypass outdated defenses. Endpoint Detection and Response (EDR) solutions monitor suspicious behavior in real time, stopping ransomware before it spreads.
2. Adopt a Zero Trust Approach
Relying on perimeter security alone is a mistake. A Zero Trust model requires verification for every access request, whether from inside or outside your network. This minimizes the damage if attackers gain entry, preventing them from moving through your systems undetected.
3. Regularly Update and Patch Systems
Outdated software is an open door for ransomware. Attackers often exploit known vulnerabilities in unpatched systems. Setting up automated patch management ensures your defenses stay up to date without relying on manual updates.
4. Train Employees on Cybersecurity Best Practices
Ransomware almost always starts with human error, often through phishing emails. Regular cybersecurity training teaches employees to spot fake emails, avoid suspicious links, and follow strong password protocols—cutting down on the easiest entry point for attackers.
5. Test and Strengthen Your Backups
A ransomware attack can cripple your business, but reliable backups can be a lifesaver. Regularly test your backup systems to ensure they’re working, and store them in a secure, offsite location that ransomware can’t reach. If an attack happens, you’ll be able to restore operations without paying a ransom.
Don’t wait for a breach to rethink your security
Businesses that fail to adapt will continue to be easy targets. Protecting your organization from ransomware requires more than just awareness—it demands action.
At GCS, we help businesses strengthen their defenses with:
✔️ Advanced endpoint protection to stop ransomware before it spreads
✔️ Real-time threat monitoring to detect suspicious activity early
✔️ Incident response solutions to minimize downtime and damage
Don’t wait for an attack—secure your business now. Contact us to build a ransomware-proof security strategy.